Ace:Prototype Audit
From Adapt
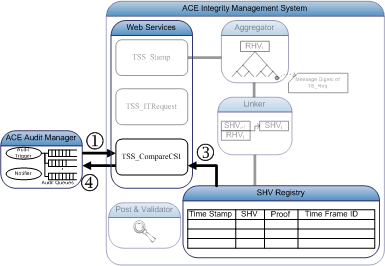
- The ACE-AM retrieves the integrity token associated with the digital object and computes the corresponding CSI value from the integrity token, followed by calling TSS_CompareCsi using the computed value and the timestamp parameters.
- The ACE-IMS retrieves the stored CSI that corresponds to the timestamp, and compares the stored CSI to the computed value.
- The comparison result is returned to the ACE-AM.
- If the comparison result is positive, the Audit Manger computes the hash of the object and compares it to the hash stored in the integrity token.