SecureShell: Difference between revisions
No edit summary |
|||
| (83 intermediate revisions by 22 users not shown) | |||
| Line 1: | Line 1: | ||
Secure Shell (or [http://en.wikipedia.org/wiki/Secure_Shell SSH]) is a network protocol allowing two computers to exchange data securely over an insecure network. By default use of SSH brings the user to a terminal, but the protocol can be used for other types of data transfer such as [[SFTP]] and [[SCP]]. | Secure Shell (or [http://en.wikipedia.org/wiki/Secure_Shell SSH]) is a network protocol allowing two computers to exchange data securely over an insecure network. By default, use of SSH brings the user to a terminal, but the protocol can be used for other types of data transfer such as [[SFTP]] and [[SCP]]. | ||
==Connecting to an SSH Server== | ==Connecting to an SSH Server== | ||
Under | Under Linux and macOS, the following command from a terminal will connect a client computer to the UMIACS [[Nexus]]. | ||
# ssh | # ssh username@nexusgroup.umiacs.umd.edu | ||
This will give you access to a terminal on any one of the [[ | '''Note: Your Nexus submission node will vary depending on your sponsorship. See [[Nexus#Access|Nexus Access]] for more information.''' | ||
This will give you access to a terminal on any one of the [[Nexus]] servers. Note that by default you will not have access to applications that require X11 to run. | |||
All UMIACS-supported Windows hosts are installed with [http://www.chiark.greenend.org.uk/~sgtatham/putty/ PuTTY]. If you are using a self-supported machine, you can either download and install PuTTY yourself, or if you are running a [https://docs.microsoft.com/en-us/lifecycle/products/windows-10-enterprise-and-education currently supported version of Windows], you can install the OpenSSH client natively in Windows by following Microsoft's instructions [https://docs.microsoft.com/en-us/windows-server/administration/openssh/openssh_install_firstuse here]. Only the client is needed and not the server. | |||
==X11 Forwarding== | ==X11 Forwarding== | ||
By default, SSH only gives the user shell access to a host. Enabling X11 Forwarding allows users to run applications with Graphical User Interfaces. | By default, SSH only gives the user shell access to a host. Enabling X11 Forwarding allows users to run applications with Graphical User Interfaces. | ||
Under | Under Linux and macOS, the following command from a terminal will connect a client computer to the UMIACS [[Nexus]] using X11 Forwarding. Please note that under macOS, [http://xquartz.macosforge.org/landing/ xQuartz] is required on the client machine to forward X sessions from the remote session. | ||
# ssh '''- | # ssh '''-Y''' username@nexusgroup.umiacs.umd.edu | ||
'''Note: Your Nexus submission node will vary depending on your sponsorship. See [[Nexus#Access|Nexus Access]] for more information.''' | |||
'''Note: | |||
Windows | Under Windows, you will need to forward X through [http://sourceforge.net/projects/vcxsrv/ VcXsrv] or another X11 application. | ||
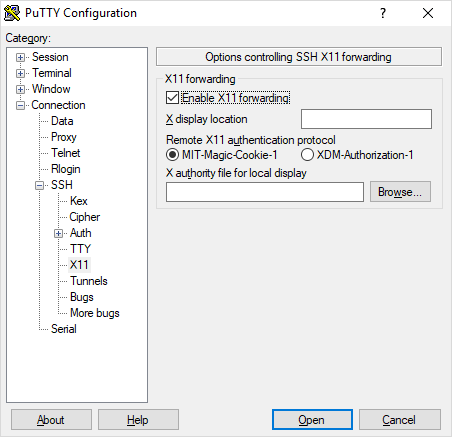
If using PuTTY, you will need to enable X forwarding. The option is under Connection > SSH > X11, shown below. | |||
[[Image:Putty-x-forwarding.png]] | |||
If using the [https://learn.microsoft.com/en-us/windows/terminal/install Windows Terminal app], you will need to set an environment variable and then relaunch the app. | |||
:<pre>setx.exe DISPLAY "127.0.0.1:0.0"</pre> | |||
After this has been done, every time you want to use X forwarding, you need to make sure VcXsrv or your other application has been started. If using VcXsrv, there will be an icon in your system tray. | |||
You will now be able to use Xwindow programs from your SSH client. | |||
==SSH Tunneling== | ==SSH Tunneling== | ||
You can tunnel one or more ports through an SSH connection such that your packets will look like they are coming from the host you are tunneling to. This is helpful for services that you would be normally blocked by a firewall. | You can tunnel one or more ports through an SSH connection such that your packets will look like they are coming from the host you are tunneling to. This is helpful for services that you would be normally blocked by a firewall. | ||
Please see the [[SecureShellTunneling]] page for more information. | Please see the [[SecureShellTunneling]] page for more information. | ||
==Passwordless SSH | ==SSH Keys (and Passwordless SSH)== | ||
SSH can utilize public key encryption to authenticate and authorize users. This can be considered more secure especially if you secure your private key with a pass-phrase. The keys themselves are not susceptible to brute force attacks like normal passwords over SSH are. | |||
Please see the [[SSH/Keys]] page for more information. | |||
'''Note: UMIACS still requires multi-factor authentication if you are connecting from the public internet or a [[VPN]] for security reasons. SSH keys can only be used when connecting to a UMIACS-supported host from another host already within UMIACS' network border.''' | |||
The | ==Verify remote host SSH fingerprint== | ||
The SSH protocol relies on host keys to verify the identify of a given host. Each host as a unique key for the various different protocols supported. | |||
When connecting to a remove host for the first time, or when the remote host's local host key configuration has changed, you may see the following prompt: | |||
<pre> | |||
$ ssh username@nexusgroup.umiacs.umd.edu | |||
The authenticity of host 'nexusgroup.umiacs.umd.edu (128.8.121.73)' can't be established. | |||
RSA key fingerprint is 25:83:aa:df:f5:ad:5f:08:c9:8a:a3:5d:97:8b:48:1f. | |||
Are you sure you want to continue connecting (yes/no)? | |||
</pre> | |||
It is considered best practice to verify the key fingerprint with the actual key of the host. UMIACS maintains a reference of SSH key fingerprints available at the following link: | |||
https://intranet.umiacs.umd.edu/hostkeys | |||
It is important to note that each key type has a different fingerprint. Depending on your local configuration, your client may prefer a specific type of key. The following commands can be used to determine the fingerprint of a given key type on a remote host: | |||
<pre> | |||
$ ssh-keyscan -t rsa nexusgroup.umiacs.umd.edu > key | |||
# nexusgroup.umiacs.umd.edu:22 SSH-2.0-OpenSSH_8.0 | |||
$ ssh-keygen -l -E md5 -f key | |||
2048 MD5:25:83:aa:df:f5:ad:5f:08:c9:8a:a3:5d:97:8b:48:1f nexusgroup.umiacs.umd.edu (RSA) | |||
</pre> | |||
If you | If you have any questions, or notice a discrepancy, please [[HelpDesk | contact staff]]. | ||
===Windows / PuTTY Verification=== | |||
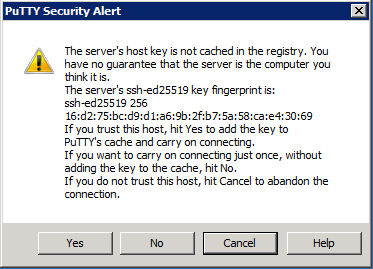
If you use PuTTY to connect to remote hosts, the prompt will be similar to the following: | |||
[[File:Putty ssh host key prompt.png]] | |||
If the host key reported by PuTTY matches the [https://gitlab.umiacs.umd.edu/staff/ssh-fingerprints/blob/master/fingerprints Documented entry for that host], it is safe to click 'yes'. If you notice a discrepancy, please [[HelpDesk | contact staff]]. | |||
===Other Platforms=== | |||
* [https://winscp.net/eng/docs/faq_hostkey WinSCP] | |||
* [https://mobaxterm.mobatek.net/ MobaXterm] | |||
==Long Running Processes== | |||
If you are dealing with a long running process that is inhibiting your ability to work regularly, you may want to run your processes inside a screen on the host that you're connecting to. This way, if the connection is dropped for any reason the screen session will automatically detach on the host and will continue running so that you can reattach it at a later time when you've connected again. Please see our documentation on [[Screen | GNU Screen]] for more information. | |||
==Further Information== | ==Further Information== | ||
[ | * [https://www.openssh.com/ OpenSSH] | ||
* [https://docs.microsoft.com/en-us/windows-server/administration/openssh/openssh_install_firstuse OpenSSH on Windows] | |||
[ | |||
Latest revision as of 20:35, 11 September 2025
Secure Shell (or SSH) is a network protocol allowing two computers to exchange data securely over an insecure network. By default, use of SSH brings the user to a terminal, but the protocol can be used for other types of data transfer such as SFTP and SCP.
Connecting to an SSH Server
Under Linux and macOS, the following command from a terminal will connect a client computer to the UMIACS Nexus.
# ssh username@nexusgroup.umiacs.umd.edu Note: Your Nexus submission node will vary depending on your sponsorship. See Nexus Access for more information.
This will give you access to a terminal on any one of the Nexus servers. Note that by default you will not have access to applications that require X11 to run.
All UMIACS-supported Windows hosts are installed with PuTTY. If you are using a self-supported machine, you can either download and install PuTTY yourself, or if you are running a currently supported version of Windows, you can install the OpenSSH client natively in Windows by following Microsoft's instructions here. Only the client is needed and not the server.
X11 Forwarding
By default, SSH only gives the user shell access to a host. Enabling X11 Forwarding allows users to run applications with Graphical User Interfaces.
Under Linux and macOS, the following command from a terminal will connect a client computer to the UMIACS Nexus using X11 Forwarding. Please note that under macOS, xQuartz is required on the client machine to forward X sessions from the remote session.
# ssh -Y username@nexusgroup.umiacs.umd.edu Note: Your Nexus submission node will vary depending on your sponsorship. See Nexus Access for more information.
Under Windows, you will need to forward X through VcXsrv or another X11 application.
If using PuTTY, you will need to enable X forwarding. The option is under Connection > SSH > X11, shown below.
If using the Windows Terminal app, you will need to set an environment variable and then relaunch the app.
setx.exe DISPLAY "127.0.0.1:0.0"
After this has been done, every time you want to use X forwarding, you need to make sure VcXsrv or your other application has been started. If using VcXsrv, there will be an icon in your system tray.
You will now be able to use Xwindow programs from your SSH client.
SSH Tunneling
You can tunnel one or more ports through an SSH connection such that your packets will look like they are coming from the host you are tunneling to. This is helpful for services that you would be normally blocked by a firewall.
Please see the SecureShellTunneling page for more information.
SSH Keys (and Passwordless SSH)
SSH can utilize public key encryption to authenticate and authorize users. This can be considered more secure especially if you secure your private key with a pass-phrase. The keys themselves are not susceptible to brute force attacks like normal passwords over SSH are.
Please see the SSH/Keys page for more information.
Note: UMIACS still requires multi-factor authentication if you are connecting from the public internet or a VPN for security reasons. SSH keys can only be used when connecting to a UMIACS-supported host from another host already within UMIACS' network border.
Verify remote host SSH fingerprint
The SSH protocol relies on host keys to verify the identify of a given host. Each host as a unique key for the various different protocols supported.
When connecting to a remove host for the first time, or when the remote host's local host key configuration has changed, you may see the following prompt:
$ ssh username@nexusgroup.umiacs.umd.edu The authenticity of host 'nexusgroup.umiacs.umd.edu (128.8.121.73)' can't be established. RSA key fingerprint is 25:83:aa:df:f5:ad:5f:08:c9:8a:a3:5d:97:8b:48:1f. Are you sure you want to continue connecting (yes/no)?
It is considered best practice to verify the key fingerprint with the actual key of the host. UMIACS maintains a reference of SSH key fingerprints available at the following link: https://intranet.umiacs.umd.edu/hostkeys
It is important to note that each key type has a different fingerprint. Depending on your local configuration, your client may prefer a specific type of key. The following commands can be used to determine the fingerprint of a given key type on a remote host:
$ ssh-keyscan -t rsa nexusgroup.umiacs.umd.edu > key # nexusgroup.umiacs.umd.edu:22 SSH-2.0-OpenSSH_8.0 $ ssh-keygen -l -E md5 -f key 2048 MD5:25:83:aa:df:f5:ad:5f:08:c9:8a:a3:5d:97:8b:48:1f nexusgroup.umiacs.umd.edu (RSA)
If you have any questions, or notice a discrepancy, please contact staff.
Windows / PuTTY Verification
If you use PuTTY to connect to remote hosts, the prompt will be similar to the following:
If the host key reported by PuTTY matches the Documented entry for that host, it is safe to click 'yes'. If you notice a discrepancy, please contact staff.
Other Platforms
Long Running Processes
If you are dealing with a long running process that is inhibiting your ability to work regularly, you may want to run your processes inside a screen on the host that you're connecting to. This way, if the connection is dropped for any reason the screen session will automatically detach on the host and will continue running so that you can reattach it at a later time when you've connected again. Please see our documentation on GNU Screen for more information.