Duo: Difference between revisions
No edit summary |
No edit summary |
||
| (37 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
[https://www.duo.com Duo] is the multi-factor authentication (MFA) solution for both UMD centralized information technology resources ( | [https://www.duo.com Duo] is the multi-factor authentication ([[MFA]]) solution for both UMD centralized information technology resources (DIT) and UMIACS local resources. Multi-factor solutions ensure that you have something you know (i.e. your password) and something you have (phone/tablet/token) when trying to authenticate. This ensures that phishing and other attempts to secure your password do not result in an account compromise and protect you and your data from unauthorized access. | ||
Enrollment is discrete and must be done for both UMD (if you have a UMD appointment) and UMIACS. | '''Enrollment is discrete and must be done for both UMD (if you have a UMD appointment) and UMIACS individually.''' You can enroll the same phone for both of these services, but not the same hardware token (if you use a token for UMD already). The UMIACS Single Sign-On and requires Duo authentication. | ||
'''Do not share a registered Duo authentication factor with any other individual for any purpose. Action may be taken against your account if you do so.''' | |||
[[File:duo_login.png|400px|thumb|left|Duo Login Prompt]] | [[File:duo_login.png|400px|thumb|left|Duo Login Prompt]] | ||
==Enrollment== | ==Enrollment== | ||
Please refer to Duo's [https://guide.duo.com/enrollment Enrollment] guide which has comprehensive information on how enroll your devices. | Please refer to Duo's [https://guide.duo.com/enrollment Enrollment] guide which has comprehensive information on how to enroll your devices. Your initial sign in for enrollment purposes '''must''' be done via our [https://intranet.umiacs.umd.edu/directory/auth/login Directory application]. | ||
We encourage users to enroll with their smart phone as it provides the most seamless experience | We encourage users to enroll with their smart phone as it provides the most seamless experience. We also support iOS/Android Tablets, landlines, and U2F [https://fidoalliance.org/certification/fido-certified-products/ FIDO] authenticator tokens (though these do not work with our MFA SSH service). | ||
==Management== | ==Management== | ||
Users can manage their UMIACS Duo settings as part of the required login to the [https://intranet.umiacs.umd.edu/directory/info Directory Application]. Please follow the Duo guide for [https://guide.duo.com/manage-devices Managing Devices] when you see the Duo login prompt. | Users can manage their UMIACS Duo settings as part of the required login to the [https://intranet.umiacs.umd.edu/directory/info Directory Application]. Please follow the Duo guide for [https://guide.duo.com/manage-devices Managing Devices] when you see the Duo login prompt. | ||
We suggest | We suggest you register using a mobile phone or tablet that is always in your personal possession. If/When you upgrade or dispose of your currently registered phone/tablet, please consider enrolling your new device before getting rid of your old device. Activation of your new device will require you to successfully authenticate with a currently registered device. If you no longer have the device but have kept the same phone number, you can select <b>Call Me</b> to have Duo call you to authenticate your session to manage/enroll your devices. If you do not have access to your previous device(s) or the phone number, you will need to [[HelpDesk | contact staff]] for assistance. | ||
==Offline Use== | |||
<gallery mode="packed-hover" widths=260px heights=260px style="float:right;"> | |||
Image:duo_offline1.png|Duo Offline One-Time Code | |||
Image:duo_offline2.png|Entering Your Code | |||
</gallery> | |||
For use when phone data or calls are not available, there are 2 options. | |||
You may use the Duo App on their phone or tablet—without any internet connection—to generate one-time codes that will allow you to authenticate to Duo. This code will be the input for the <code>passcode</code> option in the Duo pane of web authentication. To get a code from the app, open the app and tap on the entry labeled "Duo-protected UMIACS." This will present a 6 digit passcode. | |||
Alternatively, YubiKey hardware tokens can be used with Duo. Hardware tokens must be enrolled by the Technical staff, so if you are interested in procuring a hardware token for use with Duo, please [[HelpDesk | contact staff]]. '''We only support registering YubiKey tokens for this purpose, no other hardware token.''' | |||
==Services== | ==Services== | ||
| Line 20: | Line 34: | ||
<div style="column-count:2;-moz-column-count:2;-webkit-column-count:2"> | <div style="column-count:2;-moz-column-count:2;-webkit-column-count:2"> | ||
* [[GitLab]] | * [[GitLab]] | ||
* [[ | * [[Jira]] | ||
* [ | * [[OBJ | Object Storage]] | ||
* [https://intranet.umiacs.umd.edu/directory Directory] | |||
* [https://intranet.umiacs.umd.edu/requests Requests] | * [https://intranet.umiacs.umd.edu/requests Requests] | ||
* [ | * MediaWiki logins | ||
* [[SecureShell/MFA | SSH]] (when coming in from off-campus) | |||
</div> | </div> | ||
==FAQ== | ==FAQ== | ||
;I can no longer clone HTTPS Git repositories in [[GitLab]] | ; I can no longer clone HTTPS Git repositories in [[GitLab]]. How do I work around this? | ||
: Since we require more than just your username/password to log into [[GitLab]] you | : Since we now require more than just your username/password to log into [[GitLab]], you cannot use your UMIACS credentials directly for accessing HTTPS Git repositories. We encourage you to setup an [https://gitlab.umiacs.umd.edu/help/ssh/README.md#ssh SSH key] instead. If you have a case where you need to use HTTPS, you can use a [https://gitlab.umiacs.umd.edu/help/user/profile/personal_access_tokens.md Personal Access Token] to accomplish this. Ensure that you create the token with <code>API</code> scope. You would then use your username as normal and use the token as the password. Treat this token as a personal secret, as it is sufficient to act as your account within GitLab. | ||
; How do I authenticate with a Token? | |||
: We only currently support YubiKey tokens for our Duo deployment. You can follow the instructions from [https://guide.duo.com/tokens Yubico]; you will need to tap the YubiKey once you select the '''Enter a Passcode''' field. It will create a passcode (will look something like ''kffuastenhldrhfhadafdarivuntddugrvjvllddjjuget'') and send a return. | |||
Latest revision as of 20:53, 18 February 2025
Duo is the multi-factor authentication (MFA) solution for both UMD centralized information technology resources (DIT) and UMIACS local resources. Multi-factor solutions ensure that you have something you know (i.e. your password) and something you have (phone/tablet/token) when trying to authenticate. This ensures that phishing and other attempts to secure your password do not result in an account compromise and protect you and your data from unauthorized access.
Enrollment is discrete and must be done for both UMD (if you have a UMD appointment) and UMIACS individually. You can enroll the same phone for both of these services, but not the same hardware token (if you use a token for UMD already). The UMIACS Single Sign-On and requires Duo authentication.
Do not share a registered Duo authentication factor with any other individual for any purpose. Action may be taken against your account if you do so.
Enrollment
Please refer to Duo's Enrollment guide which has comprehensive information on how to enroll your devices. Your initial sign in for enrollment purposes must be done via our Directory application.
We encourage users to enroll with their smart phone as it provides the most seamless experience. We also support iOS/Android Tablets, landlines, and U2F FIDO authenticator tokens (though these do not work with our MFA SSH service).
Management
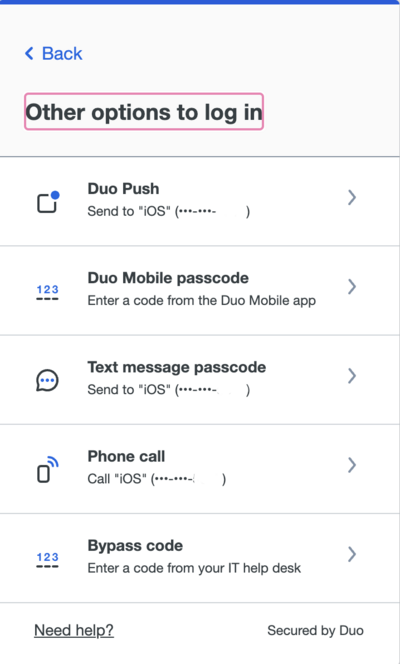
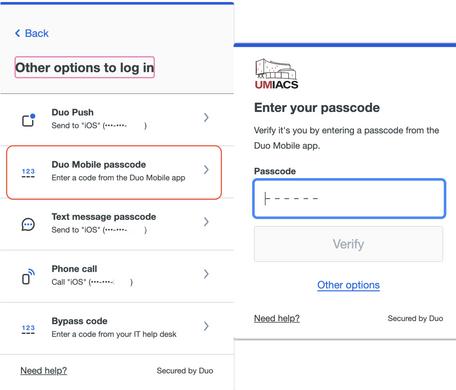
Users can manage their UMIACS Duo settings as part of the required login to the Directory Application. Please follow the Duo guide for Managing Devices when you see the Duo login prompt.
We suggest you register using a mobile phone or tablet that is always in your personal possession. If/When you upgrade or dispose of your currently registered phone/tablet, please consider enrolling your new device before getting rid of your old device. Activation of your new device will require you to successfully authenticate with a currently registered device. If you no longer have the device but have kept the same phone number, you can select Call Me to have Duo call you to authenticate your session to manage/enroll your devices. If you do not have access to your previous device(s) or the phone number, you will need to contact staff for assistance.
Offline Use
For use when phone data or calls are not available, there are 2 options.
You may use the Duo App on their phone or tablet—without any internet connection—to generate one-time codes that will allow you to authenticate to Duo. This code will be the input for the passcode option in the Duo pane of web authentication. To get a code from the app, open the app and tap on the entry labeled "Duo-protected UMIACS." This will present a 6 digit passcode.
Alternatively, YubiKey hardware tokens can be used with Duo. Hardware tokens must be enrolled by the Technical staff, so if you are interested in procuring a hardware token for use with Duo, please contact staff. We only support registering YubiKey tokens for this purpose, no other hardware token.
Services
The following UMIACS services are secured with our Duo MFA solution.
FAQ
- I can no longer clone HTTPS Git repositories in GitLab. How do I work around this?
- Since we now require more than just your username/password to log into GitLab, you cannot use your UMIACS credentials directly for accessing HTTPS Git repositories. We encourage you to setup an SSH key instead. If you have a case where you need to use HTTPS, you can use a Personal Access Token to accomplish this. Ensure that you create the token with
APIscope. You would then use your username as normal and use the token as the password. Treat this token as a personal secret, as it is sufficient to act as your account within GitLab.
- How do I authenticate with a Token?
- We only currently support YubiKey tokens for our Duo deployment. You can follow the instructions from Yubico; you will need to tap the YubiKey once you select the Enter a Passcode field. It will create a passcode (will look something like kffuastenhldrhfhadafdarivuntddugrvjvllddjjuget) and send a return.