SecureShell: Difference between revisions
No edit summary |
No edit summary |
||
| Line 6: | Line 6: | ||
This will give you access to a terminal on any one of the [[OpenLAB]] servers. Note that by default you will not have access to applications that require X11 to run. | This will give you access to a terminal on any one of the [[OpenLAB]] servers. Note that by default you will not have access to applications that require X11 to run. | ||
All UMIACS Windows hosts are installed with SSH Secure Shell Client | All UMIACS Windows hosts are installed with either the SSH Secure Shell Client or [http://www.chiark.greenend.org.uk/~sgtatham/putty/ PuTTY]. | ||
==X11 Forwarding== | ==X11 Forwarding== | ||
By default, SSH only gives the user shell access to a host. Enabling X11 Forwarding allows users to run applications with Graphical User Interfaces. | By default, SSH only gives the user shell access to a host. Enabling X11 Forwarding allows users to run applications with Graphical User Interfaces. | ||
Under Linux and macOS, the following command from a terminal will connect a client computer to the UMIACS [[OpenLAB]] using X11 Forwarding. | Under Linux and macOS, the following command from a terminal will connect a client computer to the UMIACS [[OpenLAB]] using X11 Forwarding. Please note that under macOS, [http://xquartz.macosforge.org/landing/ xQuartz] is required on the client machine to forward X sessions from the remote session. | ||
# ssh '''-Y''' bkirz@openlab.umiacs.umd.edu | # ssh '''-Y''' bkirz@openlab.umiacs.umd.edu | ||
Under | Under Windows, you will need to forward X through [http://sourceforge.net/projects/vcxsrv/ VcXsrv] or [http://www.straightrunning.com/XmingNotes/ Xming]. | ||
First, enable X forwarding on your secure ssh client. The option is under tunneling in the ssh client settings, shown below. This only has to be done once. | First, enable X forwarding on your secure ssh client. The option is under tunneling in the ssh client settings, shown below. This only has to be done once. | ||
[[Image:sshXForward.jpg]] | [[Image:sshXForward.jpg]] | ||
Next, click save in the main ssh | Next, click save in the main ssh application window to save this setting. | ||
After this has been done, every time you want to use X forwarding, you need to make sure VcXsrv or Xming has been started (it will appear in your task tray) through the start menu programs. | After this has been done, every time you want to use X forwarding, you need to make sure VcXsrv or Xming has been started (it will appear in your task tray) through the start menu programs. | ||
| Line 98: | Line 92: | ||
If you have any questions, or notice a discrepancy, please submit a request to staff@umiacs.umd.edu. | If you have any questions, or notice a discrepancy, please submit a request to staff@umiacs.umd.edu. | ||
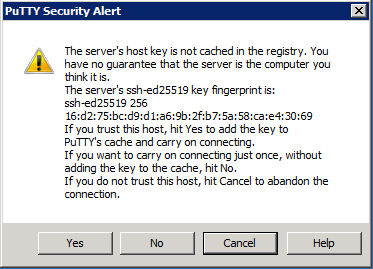
===Windows / | ===Windows / PuTTY Verification=== | ||
If you use PuTTY to connect to remote hosts, the prompt will be similar to the following: | |||
[[File:Putty ssh host key prompt.png]] | [[File:Putty ssh host key prompt.png]] | ||
If the host key reported by | If the host key reported by PuTTY matches the [https://gitlab.umiacs.umd.edu/staff/ssh-fingerprints/blob/master/fingerprints Documented entry for that host], it is safe to click 'yes'. If they do not match, please report the issue to [mailto:staff@umiacs.umd.edu staff@umiacs.umd.edu]. | ||
===Other Platforms=== | ===Other Platforms=== | ||
Revision as of 19:50, 1 October 2018
Secure Shell (or SSH) is a network protocol allowing two computers to exchange data securely over an insecure network. By default, use of SSH brings the user to a terminal, but the protocol can be used for other types of data transfer such as SFTP and SCP.
Connecting to an SSH Server
Under Linux and macOS the following command from a terminal will connect a client computer to the UMIACS OpenLAB.
# ssh bkirz@openlab.umiacs.umd.edu
This will give you access to a terminal on any one of the OpenLAB servers. Note that by default you will not have access to applications that require X11 to run.
All UMIACS Windows hosts are installed with either the SSH Secure Shell Client or PuTTY.
X11 Forwarding
By default, SSH only gives the user shell access to a host. Enabling X11 Forwarding allows users to run applications with Graphical User Interfaces.
Under Linux and macOS, the following command from a terminal will connect a client computer to the UMIACS OpenLAB using X11 Forwarding. Please note that under macOS, xQuartz is required on the client machine to forward X sessions from the remote session.
# ssh -Y bkirz@openlab.umiacs.umd.edu
Under Windows, you will need to forward X through VcXsrv or Xming.
First, enable X forwarding on your secure ssh client. The option is under tunneling in the ssh client settings, shown below. This only has to be done once.
Next, click save in the main ssh application window to save this setting.
After this has been done, every time you want to use X forwarding, you need to make sure VcXsrv or Xming has been started (it will appear in your task tray) through the start menu programs. Now, you will be able to use Xwindow programs from your ssh client.
SSH Tunneling
You can tunnel one or more ports through an SSH connection such that your packets will look like they are coming from the host you are tunneling to. This is helpful for services that you would be normally blocked by a firewall.
Please see the SecureShellTunneling page for more information.
SSH Keys (and Passwordless SSH)
There are some situations where it is important to be able to ssh without entering a password. This is mostly required when working in clusters. This is done using ssh keys. Instead of authenticating with a password, ssh can use a pre-defined set of encryption keys to establish an authorized connection. To setup passwordless ssh, do the following.
First, you will need to create a ssh key pair. It is possible to use a password that you will need to enter at the beginning of your work session. This is preferable as it is more secure but may cause problems for some clustered work, particularly our TORQUE/MAUI clusters. If you simply hit [enter], you will never be prompted for a password when ssh'ing which can lead to security problems.
- To create a passwordless key, type the following, and then hit enter to place the keys in the default directory.
# ssh-keygen -N ""
- Alternatively, to create a passphrase-protected (more-secure) key, type the following.
# ssh-keygen
This will produce two files, id_rsa and id_rsa.pub, the private and public keys, respectively. The default location will be ~/.ssh/. For the purposes of this tutorial we'll assume this default. Once you've created the keys, you will need to put them into place as follows:
# chmod 700 ~/.ssh # chmod 600 ~/.ssh/id_rsa # touch ~/.ssh/authorized_keys # chmod 600 ~/.ssh/authorized_keys # cat ~/.ssh/id_rsa.pub >> ~/.ssh/authorized_keys # rm ~/.ssh/id_rsa.pub
- It is very important that you keep your private key secure! Ensure that it is chmod'd to 600 and that you do not put it anywhere visible to other users!
- You must also make sure that no other users may write to your .ssh directory. This includes making sure that your home directory is not writable by group. Your home directory should be chmod'd to 750 or 700 to make sure of this. If the group write bit is set, your ssh keys WILL NOT WORK
If you did not select a passphrase when you generated your keys, you can now ssh without a password. If you did select a passphrase, you will need to activate the keys as follows:
# ssh-agent [SHELL] # ssh-add -t [TIME]
In this case, "[SHELL]" is your preferred shell and "[TIME]" is the amount of time you'd like the key to be active in seconds. So, the following would start a bash shell with passwordless ssh active for 30 minutes:
# ssh-agent bash # ssh-add -t 1800
You will be prompted for your passphrase and, when entered correctly, you will be able to ssh without entering a password.
To disable this functionality, simply delete your private key file (~/.ssh/id_rsa) and remove the public key from your ~/.ssh/authorized_keys2 file.
Verify remote host SSH fingerprint
The SSH protocol relies on host keys to verify the identify of a given host. Each host as a unique key for the various different protocols supported.
When connecting to a remove host for the first time, or when the remote host's local host key configuration has changed, you may see the following prompt:
$ ssh sabobbin@openlab The authenticity of host 'openlab (128.8.132.247)' can't be established. RSA key fingerprint is 25:83:aa:df:f5:ad:5f:08:c9:8a:a3:5d:97:8b:48:1f. Are you sure you want to continue connecting (yes/no)?
It is considered best practice to verify the key fingerprint with the actual key of the host. UMIACS maintains a reference of SSH key fingerprints available at the following link: https://gitlab.umiacs.umd.edu/staff/ssh-fingerprints/blob/master/fingerprints
It is important to note that each key type has a different fingerprint. Depending on your local configuration, your client may prefer a specific type of key. The following commands can be used to determine the fingerprint of a given key type on a remote host:
$ ssh-keyscan -t rsa openlab.umiacs.umd.edu > key # openlab.umiacs.umd.edu SSH-2.0-OpenSSH_7.4 $ ssh-keygen -l -f key 2048 25:83:aa:df:f5:ad:5f:08:c9:8a:a3:5d:97:8b:48:1f openlab.umiacs.umd.edu (RSA)
If you have any questions, or notice a discrepancy, please submit a request to staff@umiacs.umd.edu.
Windows / PuTTY Verification
If you use PuTTY to connect to remote hosts, the prompt will be similar to the following:
If the host key reported by PuTTY matches the Documented entry for that host, it is safe to click 'yes'. If they do not match, please report the issue to staff@umiacs.umd.edu.
Other Platforms
Long Running Processes
If you are dealing with a long running process that is inhibiting your ability to work regularly, you may want to run your processes inside a screen on the host that you're connecting to. This way, if the connection is dropped for any reason the screen session will automatically detach on the host and will continue running so that you can reattach it at a later time when you've connected again. Please see our documentation on GNU Screen for more information.