SecureShellTunneling: Difference between revisions
(Update screenshot for win7) |
(Removed references to Windows versions XP and Vista, replacing with generic 'Windows') |
||
| Line 7: | Line 7: | ||
* ssh -NfL 9999:webserver.umiacs.umd.edu:8000 openlab.umiacs.umd.edu | * ssh -NfL 9999:webserver.umiacs.umd.edu:8000 openlab.umiacs.umd.edu | ||
This example will create a local port 13389 that will be forwarded to a remote host that is running a [[RDP]] client like Windows | This example will create a local port 13389 that will be forwarded to a remote host that is running a [[RDP]] client like Windows through the host openlab.umiacs.umd.edu | ||
* ssh -L 13389:my-desktop.pc.umiacs.umd.edu:3389 openlab.umiacs.umd.edu | * ssh -L 13389:my-desktop.pc.umiacs.umd.edu:3389 openlab.umiacs.umd.edu | ||
Revision as of 19:40, 4 June 2014
Port Forwarding
When you want to just forward a specific port locally to a remote port.
This example will create a local port 9999 that will be forwarded to the remote host webbserver.umiacs.umd.edu and its port 8000 through the host openlab.umiacs.umd.edu.
- ssh -NfL 9999:webserver.umiacs.umd.edu:8000 openlab.umiacs.umd.edu
This example will create a local port 13389 that will be forwarded to a remote host that is running a RDP client like Windows through the host openlab.umiacs.umd.edu
- ssh -L 13389:my-desktop.pc.umiacs.umd.edu:3389 openlab.umiacs.umd.edu
Socks Proxy
SSH can also tunnel all traffic coming into a certain port through a SOCKS v5 proxy. Many browsers and some operating systems can be setup to then connect to this proxy to allow them again to look like they are coming from the host name you specify in your SSH command.
- ssh -ND 7777 openlab.umiacs.umd.edu
Please note: when you configure proxy settings for a browser (or your whole operating system) all the traffic for that browser (or the OS) will be sent through the proxy. This can have performance implications.
Port Forwarding with PuTTY
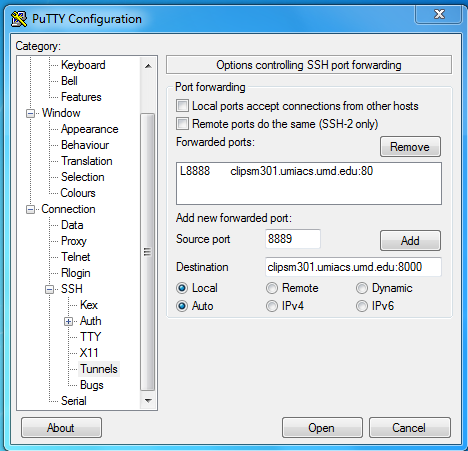
Windows users can achieve the same types of tunnels using PuTTY or a similar SSH client. In PuTTY, the port forwarding configuration dialogue can be found under "Connection>SSH>Tunnels".
This example will create a local port 8889 that is attached to the remote host clipsm301.umiacs.umd.edu on its port 8000.
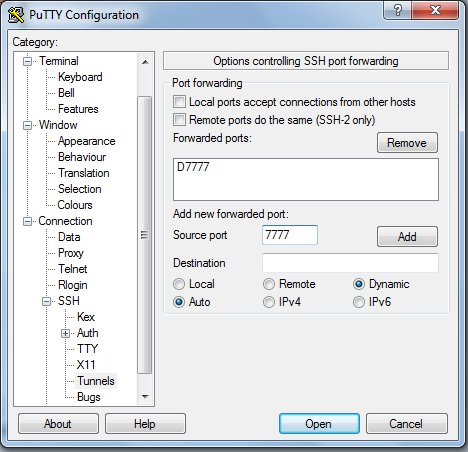
Socks Proxy with PuTTY
Windows users can tunnel traffic coming into a certain port through a SOCKS v5 proxy by using PuTTY or a similar SSH client. Many browsers and some operating systems can be setup to connect to this proxy to allow them to look like they are coming from the host name you specify.
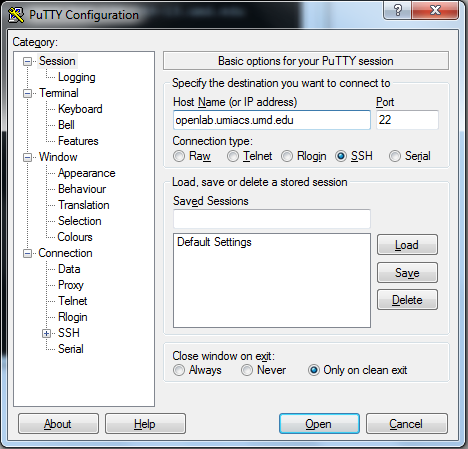
In PuTTY under "Sessions" set the Host Name:
Then under "Connection>SSH>Tunnels" enter a port number and set the type of forwarding to "Dynamic" and press add:
Click Open and log into the host. As long as this PuTTY window is open and you are logged in, you can use the SOCKS proxy.
Please note that when you configure proxy settings for a browser or your whole operating system, all the traffic for that browser or your OS will be sent through the proxy. This can have performance implications.