Ace:Prototype Object Registration
From Adapt
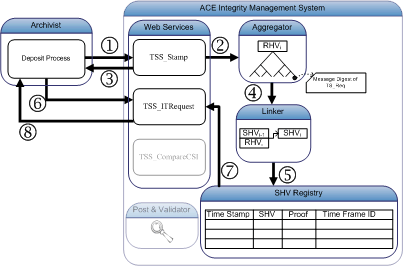
- During the last phase of the ingestion process, the deposit process (DP) initiates a request for an integrity token of the digital object by calling TSS_Stamp service of ACE-IMS while providing the message digest of the digital object as input.
- The ACE-IMS queues the request into its aggregation queue to be later processed by the Aggregator.
- The ACE-IMS sends back a receipt that contains a request id (REQID) corresponding to the request, and the expected time (ETIME) when the integrity token will be ready.
- Once the round time is up, the Aggregator gathers all the requests received, inserts random hashes if necessary, and builds an authentication tree.
- Using the root value of the aggregation tree and the previous CSI, the Aggregator computes the CSI for the current aggregation round, and stores the CSI into the CSI Registry along with the current time. Using this time value as the Time Stamp, the current CSI, and the proof of the authentication tree, the integrity token for each request is individually built.
- When ETIME has reached, DP calls TSS_ITRequest with the REQID asking for the integrity token.
- The integrity token made in Step 5 is retrieved.
- The integrity token for the digital object is finally sent back to the requester (DP).